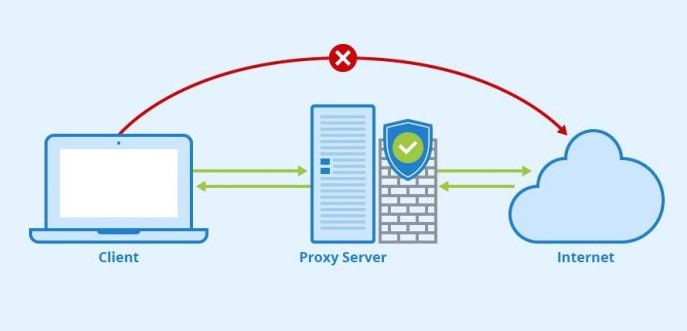
Do, you know what is an IP stresser? It is a tool that is designed to check a network/server for robustness. This can be tested by running an errand to work out whether the prevailing resources are sufficient to handle the additional load. In this article, thus, I would discuss Freebooter IP, which is an IP stresser too.
So, what is a booter?
Booter services are on-demand DDoS attack services offering by enterprising criminals to bring down websites and networks.
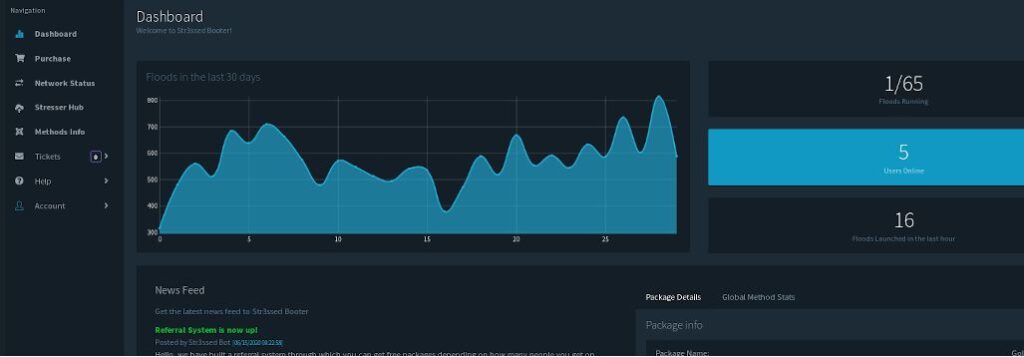
Booters come slickly pack as SaaS (Software-as-a-Service), often with email support and YouTube tutorials. Packages may offer one-time service, multiple attacks within an outlined period, or maybe “lifetime” access. A basic, one-month package can cost as little as $19.99. Payment options may include credit cards, Skrill, PayPal, or Bitcoin (through PayPal will cancel accounts if malicious intent is often proved).
Booters vs Botnets? — Freebooter IP
A botnet is a network of computers whose owners are unaware that their computers are infected with malware. And, also that it is getting used in Internet attacks. Booters are DDoS-for-hire services. While Booters traditionally use botnets to launch attacks. But, as they get more sophisticated, they’re boasting of more powerful servers to, “help you launch your attack”.
Here’s a post on How to Find IP Address of Samsung TV
Amplifications vs Reflection Attacks
Reflection and amplification attacks make use of legitimate traffic to overwhelm the network or server which is the target.
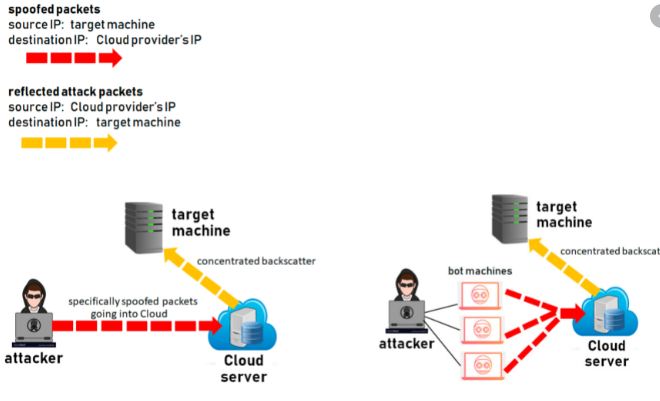
When an attacker forges the IP address of the victim and sends a message to a 3rd party while pretending to be the victim, it’s referred to as IP address spoofing. The third-party has no way of distinguishing the victim’s IP address from that of the attacker. It replies to the victim. The attacker’s IP address is hidden from both the victim and also the third-party server. This process is reflection. It is like the attacker ordering pizzas to the victim’s house while pretending to be the victim. Now the victim finishes up owing money to the pizza place for a pizza they didn’t order.
Traffic amplification happens when the attacker forces the third-party server to remit responses to the victim with the maximum amount of data possible. The ratio between the sizes of response and request is understandable because of the amplification factor. The greater this amplification, the greater the potential disruption to the victim. The third-party server is additionally disruptive due to the number of spoofed requests it’s to process. NTP Amplification is one example of such an attack.
How Denial of Service Happens
Let’s think about your home internet connection as a cafe. Your cafe is open and working 24/7 and always has some visitors. As with any building, there is a limit to how many people can fit inside. This is where internet speed comes into play.
Let’s assume a typical internet connection clocks in at 100 Mbps — and for our example, let’s say 100 Mb = 10 persons.
So we are allowed, at any given time, to have up to 10 persons inside the cafe. If we ever reach more than that 10-person limit, we are unable to accept this traffic, and thus a denial of service comes into action.
One may ask yourself how many people can these attackers simulate in a D-DoS attack. Thousands, if not tens of thousands.
SUMMING UP — Freebooter IP
While booter services cause a lot of disruption, they assist in the progression of online security. They also create a demand for security protection from companies such as Cloudflare, MVH, Sucuri, and Kalama.
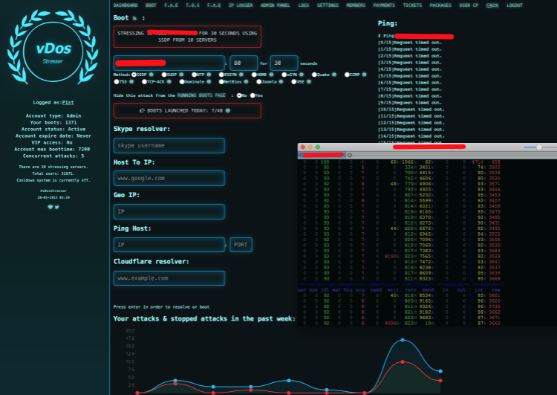
Even though the story of booter services and Skype resolvers has died for some time. There is still an existential threat of a small subset of D-DoS services that actively run. One should therefore use a VPN when using the internet.